Table of Contents
Netfilter Tutorial - How To Secure Your Qortal Router and Network Devices Connected To It
Iptables Linux firewall is used to monitor incoming and outgoing traffic to a computer and filter it based on user-defined rules to prevent anyone from accessing the computer or IP masqueraded devices. Using iptables you can define rules which will allow only selective traffic on your computer or the router itself.
What You Will Need
Before you begin with Iptables tutorial, you will need the following:
A local machine with SSH client installed. Putty https://www.putty.org/ is your best option for Windows OS while SSH client comes pre-installed on Linux OS.
Understand The Basics
All data is sent in the form packets over the internet. Linux kernel provides an interface to filter both incoming and outgoing traffic packets using tables of packet filters. Iptables is a command line application and a Linux firewall that you can use to set-up, maintain and inspect these tables. Multiple tables can be defined. Each table can contain multiple chains. A chain is nothing but a set of rules. Each rule defines what to do with the packet if it matches with that packet. When the packet is matched, it is given a TARGET. A target can be another chain to match with or one of the following special values:
ACCEPT: It means the packet will be allowed to pass through.
DROP: It means that packet will not be allowed to pass through.
RETURN: It means to skip the current chain and go back to the next rule from the chain it was called in.
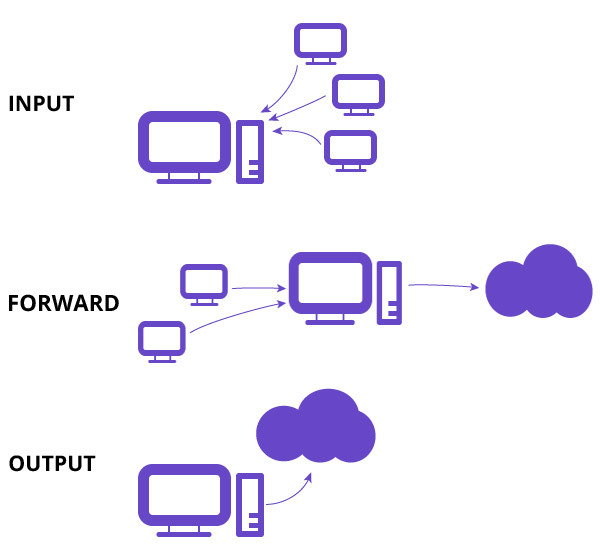
For the scope of this iptables tutorial, we are going to work with one of the default tables called filter. Filters table has three chains (sets of rules).
INPUT – This chain is used to control incoming packets to the server. You can block/allow connections based on port, protocol or source IP address.
FORWARD – This chain is used to filter packets that are incoming to the server but are to be forwarded somewhere else.
OUTPUT – This chain is used to filter packets that are going out from your server.
The Only Few Commands You Will Ever Need
This section assumes that you are already SSH'ed into the Qortal router. Look at Getting Started Getting Started
* iptables -L -v (list current firewall rules)
* iptables -F (flush all rules)
* iptables-save > /etc/iptables.rules (saves your custom rules) OR you can edit the file with nano editor /etc/rc.local and paste your rules there. Do nano /etc/rc.local, paste the rules and Ctrl + X to save and edit.
Adding Your Firewall Rules
These rules are copy and paste. Simply paste them at the Qortal terminal via SSH and save.
Block outgoing port: /sbin/iptables -A OUTPUT -p tcp –dport {PORT-NUMBER-HERE} -j DROP. For example, you want to block telnet port 21 then put 21 after –dport. It will be /sbin/iptables -A OUTPUT -p tcp –dport 21 -j DROP . Similary, if you wish to block a DNS then it's port 53. Look at common used ports by services on Wikipedia https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
Examples:
Block HTTP /sbin/iptables -A OUTPUT -p tcp –dport 80 -j DROP
Block HTTPS /sbin/iptables -A OUTPUT -p tcp –dport 443 -j DROP
Block Outoing DNS /sbin/iptables -A OUTPUT -p udp –dport 53 -j DROP
Block incoming port: /sbin/iptables -A INPUT -p tcp –destination-port {PORT-NUMBER-HERE} -j DROP. It works same as outgoing port syntax. Simply enter port numbers of running services you do not want accessed outside your network. If you wish to allow only a particular IP on any port or service then use -s IP_Address after DROP
Examples:
Block HTTP /sbin/iptables -A INPUT -p tcp –destination-port 80 -j DROP
Block HTTPS /sbin/iptables -A INPUT -p tcp –destination-port 443 -j DROP
Block HTTPS /sbin/iptables -A INPUT -p tcp -s IP_to_Block –destination-port 443 -j DROP
Monitoring Traffic Flow on Router
It is fairly simple to view what is happening on the router. The pre-installed utility "tcpdump" does all that in a human readable view. The Qortal Router comes ready with either your own recursive DNS or a DNS forwarded and to monitor all your DNS lookups, you simple paste this command in terminal:
tcpdump port 53 and '(tcp-syn|tcp-ack)!=0'
Note that port 53 is used for DNS queries. If you want to see the web site traffic, replace it with port 80.
Example for more custom firewall rules, traffic monitoring can be obtained from official Discord.
Monitoring Tor Flow on Router
The Qortal Router comes ready with your own Tor dedicated gateway. You can use it for all types of internet traffic on the router itself and on connected devices such as browsers, QT wallets, Torrents for safety and privacy which is a big deal these days.
For details on Tor access and it's utilization for connected, head over to Service Access